Security
Resiste has a security option to encrypt the values in db.properties.
This is specifically targeted at the database password, however, you can encrypt any
of the values in db.properties.
Resiste uses RSA-4096 public/private key asymmetric encryption. See my blog article for all the details.
All key generation and encryption occurs outside the the application. This means that you
are free to generate new keys and re-encrypt the db.properties values at any time.
No code changes are required.
Linux / openssl
Resiste uses openssl for generating keys and encrypting values. I've only used
openssl on Linux. I don't know if it would work on Windows, Cygwin, or other
platforms. You can try!
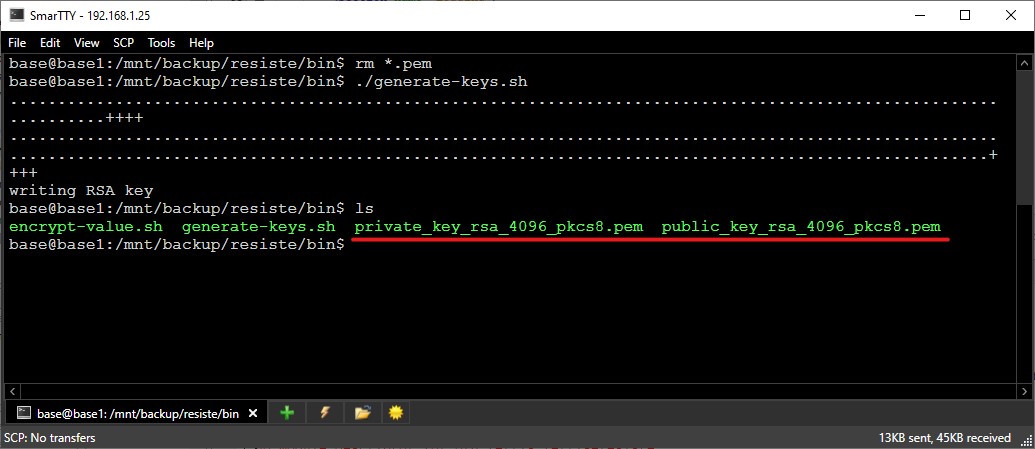
Generate Keys
The first thing you need to do is generate the public/private keys that are
used for encryption/decryption. The scripts are located in the
[RESISTE_HOME]/security/ directory. Open a shell and execute
[RESISTE_HOME]/security/generate-keys.sh directory.
That's it! Now you're ready to encrypt values.
Encrypt Value
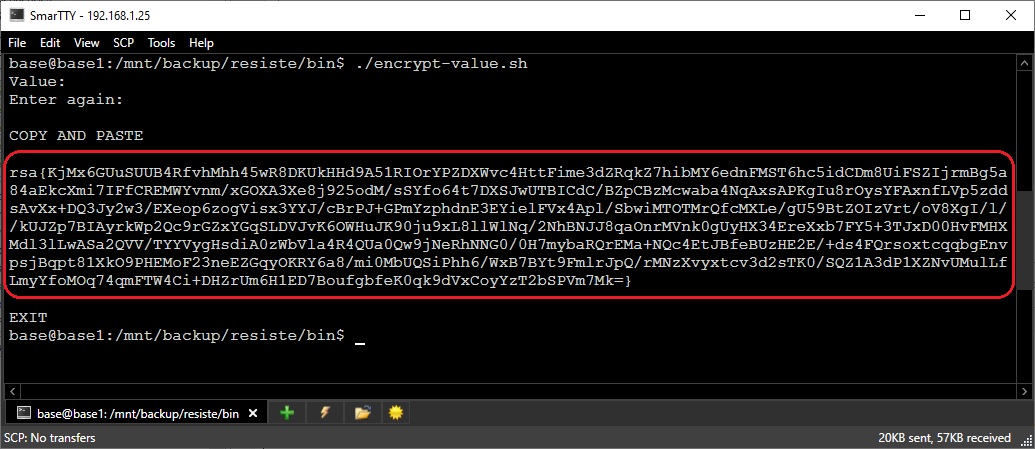
Once the keys are generated, you can use the public key to encrypt a value.
Open a shell and execute
[RESISTE_HOME]/security/encrypt-value.sh. It will prompt you twice
for the value to verify it was entered correctly. What you type will not echo
to the console. The script will output a Base64 encoded, encrypted version of
your value. Copy this entire value -
Including the beginning rsa{ and ending }.
Paste
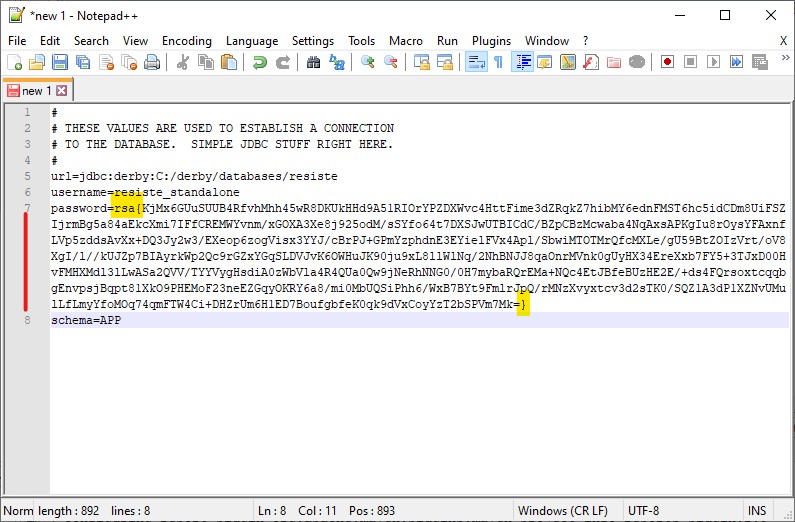
Paste the Base64 encoded, encrypted version of your value into db.properties.
Note the beginning rsa{
Note the ending }
Note it is a single value all on one line. See how the line numbers in Notepad++ expand.
Encrypt More
Any value in db.properties can be encrypted in this way. It
is not just for the password value.
Security complete! Next is scheduling.

